I had trouble communicating from the DMZ to the inside when I built a DMZ with ASA 5505 in my home laboratory.
Components
Because ASA 5505 can not use VLAN trunk without a security license, it connects to Catalyst and aggregates it on access respectively.
- Cannot communicate from DMZ to inside
- VLAN configuration of the Cisco ASA 5505
- Outside interface to no forward
- Conclusion - Can not communicate from DMZ to inside at home lab ASA
Cannot communicate from DMZ to inside
I applied an appropriate ACL to the interface and checked the communication, but I can not communicate from DMZ to inside.
The settings of interface, security level etc are as follows. The VLAN name inside is management.
ASA5505# sh run int interface Vlan1 nameif management security-level 100 ip address 192.168.1.x 255.255.255.0 ! interface Vlan50 no forward interface Vlan1 nameif dmz security-level 50 ip address 192.168.50.xx 255.255.255.0 ! interface Vlan99 description internet nameif outside security-level 0 pppoe client vpdn group nifty ip address pppoe setroute
Check here for no forward interface Vlan1
Setting of NAT and ACL is here. The number of servers is small, ACL is spread widely because it is under exam at any time. The rules of NAT have room for review.
ASA5505# sh run nat nat (outside,management) source static any any destination static interface Web-01 service OpenWeb Web nat (management,outside) source dynamic Internet-PAT interface nat (dmz,management) source static any any unidirectional //Does not work because of no forward nat (dmz,outside) source dynamic Internet-PAT interface ASA5505# sh run access-list access-list Web extended permit tcp any any eq www access-list dmz extended permit ip any any ASA5505# sh run access-group access-group Web in interface outside access-group dmz in interface dmz
Capturing with ASA internal packet tracer is as follows. The packet is being dropped by no-forward-rule.
ASA5505# packet-tracer input dmz icmp 192.168.50.x 0 0 192.168.1.x Phase: 1 Type: ROUTE-LOOKUP Subtype: Resolve Egress Interface Result: ALLOW Config: Additional Information: in 192.168.1.0 255.255.255.0 management Phase: 2 Type: ACCESS-LIST Subtype: no-forward-rule Result: DROP Config: Additional Information: Result: input-interface: dmz input-status: up input-line-status: up output-interface: management output-status: up output-line-status: up Action: drop Drop-reason: (acl-drop) Flow is denied by configured rule
Although such an ACL is not set, it is rejected by no forward of the interface setting as the output of packet tracer does.
interface Vlan50 no forward interface Vlan1
VLAN configuration of the Cisco ASA 5505
Cisco Secure Products and Solutions - Cisco
It seems to be old information, but main function does not changed in recent version.
In the setting guide, the following VLAN configuration is described.
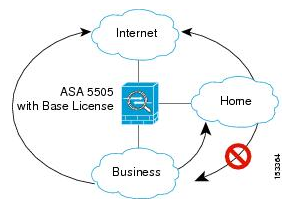
no forward interface Vlan business is set in home VLAN in the figure.
I think that it is reasonable to review this and make it no forward from the outside of the Internet connection to management (inside).
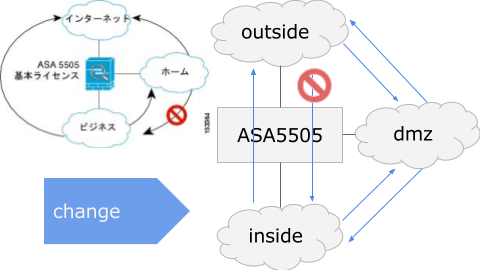
Outside interface to no forward
Traffic from DMZ to inside is necessary for various communication such as R-Proxy. Therefore, cancel the no forward of the DMZ and set no outside to outside instead.
Attempting to simply add the setting of no forward will result in an error.
ASA5505(config-if)# interface Vlan99 ASA5505(config-if)# no forward interface vlan 1 ERROR: Interface Vlan1 is already used in another no forward command ASA5505(config-if)# no forward interface vlan 50 ERROR: Interface Vlan50 is already used in another no forward command
For testing, After doing the no forward setting for the VLAN not used, it was able to set it correctly. Actual communication is no problem, It can route all between each interface. However, communication from dmz to inside requires ACL. When ACL is applied, permit is also required for internet.
I was going to throw away the communication from outside to inside (Vlan 1), but I have never been able to continue communication considering the ease of migration.
ASA5505(config-if)# no forward interface Vlan 10 ASA5505(config-if)# exit ASA5505(config)# interface Vlan50 ASA5505(config-if)# forward interface Vlan 1
The final interface settings are as follows.
ASA5505# sh run int vlan 1 ! interface Vlan1 nameif management security-level 100 ip address 192.168.1.5 255.255.255.0 ASA5505# sh run int vlan 50 ! interface Vlan50 nameif dmz security-level 50 ip address 192.168.50.1 255.255.255.0 ASA5505# sh run int vlan 99 ! interface Vlan99 description internet no forward interface Vlan10 nameif outside security-level 0 pppoe client vpdn group nifty ip address pppoe setroute
Conclusion - Can not communicate from DMZ to inside at home lab ASA
In the ASA 5505 used in the home laboratory, an event occurred in which communication from the DMZ to the inside was not possible. The problem was the influence of no forward interface, which is required for the ASA 5505 basic license. Finally, by setting no forward interface to outside and making the designated VLAN unused, it became possible to communicate between all interfaces (controlled by ACL policy).