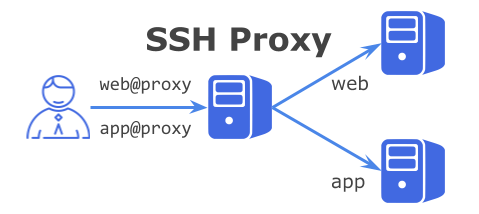
In an environment where SSH access to the server is restricted by a firewall or the like, SSH Proxy access to the backend server is established by SSH R-Proxy server (Docker container), not a step-by-step server.
There is also a method to make SSH connection via HTTP Proxy, but this time we do not use HTTP Proxy but use simple SSH R-Proxy.
SSH Piper
In this article, use this SSH Piper as SSH Proxy.
From README
Here, we assume SSH sorting on a user name basis to each personal server (container).
+---------+ +------------------+ +-----------------+
| | | | | |
| Bob +----ssh -l bob----+ | SSH Piper +-------------> Bob' machine |
| | | | | | | |
+---------+ | | | | +-----------------+
+---> pipe-by-name--+ |
+---------+ | | | | +-----------------+
| | | | | | | |
| Alice +----ssh -l alice--+ | +-------------> Alice' machine |
| | | | | |
+---------+ +------------------+ +-----------------+
Downstream SSH Piper Upstream
What we expect is an operation like HTTP reverse proxy, but in SSH it can not be routed in the host header like HTTP, so it will behave like a reverse proxy with login user name.
Build SSH Piper with Docker
SSH Piper is provided as a Docker Image. This makes it possible to skip the execution environment setting of Go language and so on.
Directory / File tree
$ sudo tree -pug . ├── [-rw-r--r-- root root ] README.md ├── [drwxr-xr-x root root ] config │ └── [drwxr-xr-x root root ] sshpiper │ ├── [drwx------ root root ] asa │ │ └── [-rw------- root root ] sshpiper_upstream │ └── [drwx------ root root ] centos7 │ └── [-rw------- root root ] sshpiper_upstream └── [-rw-r--r-- root root ] docker-compose.yml
docker-compose.yml looks like this.
$ cat ./docker-compose.yml version: '2' #https://github.com/tg123/sshpiper services: external: image: farmer1992/sshpiperd container_name: sshpiper ports: - "2222:2222" volumes: - /etc/ssh/ssh_host_rsa_key:/etc/ssh/ssh_host_rsa_key:ro - ./config/sshpiper:/var/sshpiper
As you can see in detail, you need to be careful with Config Permission . The Config file is 700/600.
$ sudo chmod 700 config/sshpiper/asa $ sudo chmod 600 ./config/sshpiper/asa/sshpiper_upstream $ sudo ls -la ./config/sshpiper/asa/ 合計 4 drwx------. 2 root root 31 4月 30 10:57 . drwxr-xr-x. 4 root root 28 4月 30 10:56 .. -rw-------. 1 root root 36 4月 30 10:57 sshpiper_upstream $ sudo cat ./config/sshpiper/asa/sshpiper_upstream # Cisco ASA5505 dev@192.168.1.5:22
SSH Proxy operation confirmation
Activate SSH Piper 's Docker container and check its operation.
$ docker-compose up <Another Terminal> $ ssh 192.168.1.76 -p 2222 -l asa asa@192.168.1.76's password: Type help or '?' for a list of available commands. ASA5505> $ ssh 192.168.1.76 -p 2222 -l centos7 centos7@192.168.1.76's password: [dev@CentOS7-01 ~]$
Although the above is a log from Linux, SSH access is possible from TeraTerm and other terminals as well. At the password input prompt, SSH Piper's display is displayed, but if the connection succeeds, you can connect to the upstream server (NW device).
The access log of SSH Piper is as follows. The user name and upstream (back end) server are mapped.
sshpiper | 2018/04/30 02:03:09 sshpiperd started sshpiper | 2018/04/30 02:03:10 connection accepted: 192.168.1.111:60508 sshpiper | 2018/04/30 02:03:10 mapping user [asa] to [dev@192.168.1.5:22]
Unusable if Permission is incorrect
Permission in the sshpiper_upstream file needs to be restricted like.ssh. If Permission is inappropriate, SSH connection fails with perm is too open error as in the following log.
$ sudo docker-compose up Creating network "sshpiper_default" with the default driver Creating sshpiper ... Creating sshpiper ... done Attaching to sshpiper sshpiper | sshpiperd by Boshi Lian<farmer1992@gmail.com> sshpiper | https://github.com/tg123/sshpiper sshpiper | <snip> sshpiper | 2018/04/30 01:59:23 sshpiperd started sshpiper | 2018/04/30 01:59:25 connection accepted: 192.168.1.111:60436 sshpiper | 2018/04/30 01:59:25 connection from 192.168.1.111:60436 establishing failed reason: /var/sshpiper/asa/sshpiper_upstream's perm is too open
TODO
- Access control to SSH Piper User control
- Login with SSH secret key (non-password authentication)
- Access log management
- etc.
Conclusion - Build SSH R-Proxy with SSH Piper w/Docker
I was able to build SSH Proxy with SSH Piper. Although the access control related verification is still necessary, it can be used as a simple SSH Proxy, so it is considered very useful for avoiding various restrictions such as Firewall.