
This article tested Internet access speedup by IPv6 connection, but IPv6 Plus (MAP-E) provided by @nifty requires dedicated equipment, the Cisco ASA5505, VyOS, Linux etc. can only perform simple IPoE connection , It was not possible to speedup the IPv4 service.
en-designetwork.hatenablog.com
Services and Web sites to be used on a daily basis Since IPv4 access is required for the majority of Web sites, we will build an environment of IPv4 over IPv6 tunnel using the DS-Lite service of ZOOT NATIVE (Interlink).
The DS-Lite service of ZOOT NATIVE is a provider-like service that enables connection to transix provided by Internet multifeed. (Japanese services)
無料体験・即日ID発行のプロバイダ - 株式会社インターリンク【公式】
- Network diagram
- NIC configuration
- Firewall configuration for NIC
- Disable SELinux
- Routing activation at CentOS
- IPv6 address and communication confirmation
- IPv4 over IPv6 tunnel setting
- Communication confirmation
- Speed comparison
- You can also use IPoE
- Conclusion - DS-Lite (IPv4 over IPv6) Internet connection with CentOS
Network diagram
Use Catalyst2960 (L2SW) for changing multiple routers connect to the Internet.
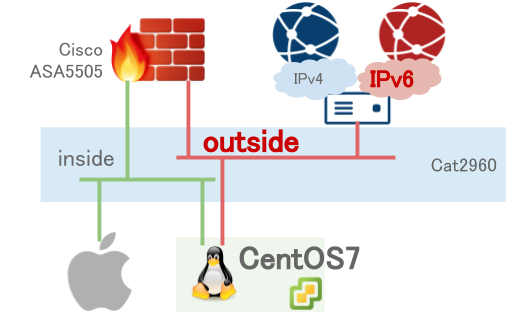
NIC configuration
- inside NIC
$ sudo cat /etc/sysconfig/network-scripts/ifcfg-ens160 TYPE=Ethernet BOOTPROTO=none DEFROUTE=no IPV4_FAILURE_FATAL=yes IPV6INIT=yes IPV6_AUTOCONF=no IPV6_DEFROUTE=yes IPV6_FAILURE_FATAL=no IPV6_ADDR_GEN_MODE=stable-privacy NAME=ens160 UUID=531a8e7d-07d1-4b71-9d27-96433ca6f8fc DEVICE=ens160 ONBOOT=yes DNS1=192.168.1.77 DNS2=8.8.8.8 DOMAIN=designet.local ZONE=trusted IPADDR=192.168.1.8 PREFIX=24 IPV6_PRIVACY=no
- outside physical NIC
Use Sub Interfaces because outside NIC is shared some segments.
$ sudo cat /etc/sysconfig/network-scripts/ifcfg-ens192 TYPE=Ethernet DEFROUTE=yes IPV4_FAILURE_FATAL=no IPV6INIT=no IPV6_AUTOCONF=yes IPV6_DEFROUTE=yes IPV6_FAILURE_FATAL=no IPV6_ADDR_GEN_MODE=stable-privacy NAME=ens192 UUID=05c28633-5849-4892-bdc0-08e69b574ac1 DEVICE=ens192 ONBOOT=yes ZONE=trusted PEERDNS=yes PEERROUTES=yes IPV6_PEERDNS=yes IPV6_PEERROUTES=yes IPV6_PRIVACY=no
- outside Sub Interface
$ sudo cat /etc/sysconfig/network-scripts/ifcfg-outside VLAN=yes TYPE=Vlan PHYSDEV=ens192 VLAN_ID=99 REORDER_HDR=yes GVRP=no MVRP=no IPV6INIT=yes IPV6_AUTOCONF=yes IPV6_DEFROUTE=yes IPV6_FAILURE_FATAL=no IPV6_ADDR_GEN_MODE=stable-privacy NAME=outside UUID=9e20f5e5-3a57-4441-9b78-cb784c42d3fe ONBOOT=yes ZONE=trusted IPV6_PEERDNS=yes IPV6_PEERROUTES=yes
Firewall configuration for NIC
Test in no security.
$ sudo firewall-cmd --zone=trusted --change-interface=ens160 The interface is under control of NetworkManager, setting zone to 'trusted'. success $ sudo firewall-cmd --zone=trusted --change-interface=ens192 The interface is under control of NetworkManager, setting zone to 'trusted'. success $ sudo firewall-cmd --zone=trusted --change-interface=ens192.99 The interface is under control of NetworkManager, setting zone to 'trusted'. success
Disable SELinux
$ sudo setenforce 0 $ getenforce Permissive
Routing activation at CentOS
Temporary enable routing for test.
$ cat /proc/sys/net/ipv4/ip_forward 0 $ su - # echo 1 >/proc/sys/net/ipv4/ip_forward # cat /proc/sys/net/ipv4/ip_forward 1
IPv6 address and communication confirmation
- IPv6 address
I got the IPv6 global address: 2409:10:24e0:2000::/64
$ ip -6 a
15: ens192.99@ens192: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 state UP qlen 1000
inet6 2409:10:24e0:2000:b8bb:e04d:d79a:xxxx/64 scope global noprefixroute dynamic
valid_lft 2591913sec preferred_lft 604713sec
inet6 fe80::2fc9:356d:ef33:cee9/64 scope link
valid_lft forever preferred_lft forever
- IPv6 neighbor
$ ip -6 neigh fe80::221:d8ff:fe9a:d1c1 dev ens192.99 lladdr 00:21:d8:9a:d1:c1 router REACHABLE
- IPv6 default route
$ ip -6 r default via fe80::221:d8ff:fe9a:d1c1 dev ens192.99 proto static metric 400
- DS-Lite communication confirmation
Check your connectivity to Tunnel Destination.
$ ping6 2404:8e00::feed:100 PING 2404:8e00::feed:100(2404:8e00::feed:100) 56 data bytes 64 bytes from 2404:8e00::feed:100: icmp_seq=1 ttl=59 time=5.71 ms 64 bytes from 2404:8e00::feed:100: icmp_seq=2 ttl=59 time=2.71 ms ^C --- 2404:8e00::feed:100 ping statistics --- 2 packets transmitted, 2 received, 0% packet loss, time 1001ms rtt min/avg/max/mdev = 2.719/4.216/5.713/1.497 ms $ traceroute6 2404:8e00::feed:100 traceroute to 2404:8e00::feed:100 (2404:8e00::feed:100), 30 hops max, 80 byte packets 1 2409:10:24e0:2000::fffe (2409:10:24e0:2000::fffe) 1.071 ms 1.061 ms 1.581 ms 2 * * * 3 * * * 4 * * * 5 * * * 6 2404:8e00:feed:ff07::2 (2404:8e00:feed:ff07::2) 5.506 ms 10.365 ms 9.893 ms 7 2404:8e00::feed:100 (2404:8e00::feed:100) 17.772 ms 17.704 ms 11.916 ms
If it can not be connected successfully, restart the Network etc.
$ sudo systemctl restart network
IPv4 over IPv6 tunnel setting
I tried settings with help .
$ ip -6 tunnel help
Usage: ip -f inet6 tunnel { add | change | del | show } [ NAME ]
[ mode { ip6ip6 | ipip6 | ip6gre | vti6 | any } ]
[ remote ADDR local ADDR ] [ dev PHYS_DEV ]
[ encaplimit ELIM ]
[ hoplimit TTL ] [ tclass TCLASS ] [ flowlabel FLOWLABEL ]
[ dscp inherit ]
[ [i|o]seq ] [ [i|o]key KEY ] [ [i|o]csum ]
- Configuration command
Create tunnel.
$ sudo ip -6 tunnel add ds-lite mode ipip6 remote 2404:8e00::feed:100 local 2409:10:24e0:2000:b8bb:e04d:d79a:xxxx dev ens192.99
Disable input packet from the internet. (Return packets are permitted)
$ sudo firewall-cmd --zone=drop --change-interface=ds-lite success
Activate tunnel.
$ sudo ip link set dev ds-lite up
- IPv4 routing (default route) setting
$ sudo ip route add 0.0.0.0/0 dev ds-lite
- status check
$ ip a
77: ds-lite@if4: <POINTOPOINT,NOARP,UP,LOWER_UP> mtu 1452 qdisc noqueue state UNKNOWN qlen 1
link/tunnel6 2409:10:24e0:2000:b8bb:e04d:d79a:4a82 peer 2404:8e00::feed:100
inet6 fe80::9805:daff:fe9c:5d8b/64 scope link
valid_lft forever preferred_lft forever
$ ip -6 tunnel show
ip6tnl0: ipv6/ipv6 remote :: local :: encaplimit 0 hoplimit 0 tclass 0x00 flowlabel 0x00000 (flowinfo 0x00000000)
ds-lite: ip/ipv6 remote 2404:8e00::feed:100 local 2409:10:24e0:2000:b8bb:e04d:d79a:4a82 dev if4 encaplimit 4 hoplimit 64 tclass 0x00 flowlabel 0x00000 (flowinfo 0x00000000)
$ ip r
default dev ds-lite scope link
192.168.1.0/24 dev ens160 proto kernel scope link src 192.168.1.8 metric 100
Communication confirmation
Success connect to the Internet via DS-Lite.
$ traceroute 8.8.8.8 traceroute to 8.8.8.8 (8.8.8.8), 30 hops max, 60 byte packets 1 ike-gw00.transix.jp (14.0.9.66) 3.063 ms 2.763 ms 2.737 ms 2 ike-bbrt10.transix.jp (14.0.9.65) 2.994 ms 2.927 ms 2.940 ms 3 210.173.176.243 (210.173.176.243) 3.799 ms 3.778 ms 3.747 ms 4 108.170.242.129 (108.170.242.129) 3.877 ms 108.170.242.97 (108.170.242.97) 4.138 ms 108.170.242.129 (108.170.242.129) 3.725 ms 5 108.170.236.179 (108.170.236.179) 4.530 ms 108.170.236.195 (108.170.236.195) 4.575 ms 216.239.54.21 (216.239.54.21) 4.622 ms 6 google-public-dns-a.google.com (8.8.8.8) 4.211 ms 4.377 ms 4.341 ms
I can communicate from inside Mac via CentOS 7 in the same way.
Mac: $ traceroute 8.8.8.8
traceroute to 8.8.8.8 (8.8.8.8), 64 hops max, 52 byte packets
1 o-cent-rt01.designet.local (192.168.1.8) 2.404 ms 0.978 ms 1.001 ms
2 ike-gw00.transix.jp (14.0.9.66) 3.785 ms 3.350 ms 6.000 ms
3 ike-bbrt10.transix.jp (14.0.9.65) 4.419 ms 4.177 ms 4.495 ms
4 210.173.176.243 (210.173.176.243) 5.231 ms 4.827 ms 5.182 ms
5 108.170.242.193 (108.170.242.193) 5.537 ms
108.170.242.97 (108.170.242.97) 5.386 ms 5.042 ms
6 72.14.236.107 (72.14.236.107) 5.284 ms
209.85.143.51 (209.85.143.51) 5.706 ms
216.239.41.247 (216.239.41.247) 5.453 ms
7 google-public-dns-a.google.com (8.8.8.8) 5.106 ms 4.944 ms 5.183 ms
Speed comparison
Compare the communication speed between conventional IPv4 PPPoE and ZOOT NATIVE DS-Lite (IPv4 over IPv6).
Previously IPv4 PPPoE
@nifty IPv4 PPPoE + Cisco ASA 5505
-> about 5.8 Mbps

ZOOT NATIVE DS-Lite
ZOOT NATIVE DS-Lite + CentOS 7
-> About 66 Mbps

Also, traceroute results is slow in previous PPPoE. DS-Lite results are avobe.
Mac: $ traceroute 8.8.8.8
traceroute to 8.8.8.8 (8.8.8.8), 64 hops max, 52 byte packets
1 asa5505 (192.168.1.5) 9.144 ms 1.565 ms 1.376 ms
2 133.160.170.13 (133.160.170.13) 36.559 ms 44.012 ms 174.003 ms
3 133.160.170.117 (133.160.170.117) 174.886 ms 130.233 ms 177.554 ms
4 133.160.148.209 (133.160.148.209) 189.458 ms 171.760 ms 87.412 ms
5 133.160.182.129 (133.160.182.129) 170.154 ms
133.160.182.41 (133.160.182.41) 143.139 ms
133.160.182.33 (133.160.182.33) 174.666 ms
6 210.173.176.245 (210.173.176.245) 43.980 ms 131.435 ms 37.133 ms
7 108.170.242.193 (108.170.242.193) 137.539 ms 38.798 ms
108.170.242.97 (108.170.242.97) 135.910 ms
8 209.85.255.33 (209.85.255.33) 177.034 ms
72.14.236.129 (72.14.236.129) 41.840 ms
209.85.255.173 (209.85.255.173) 37.989 ms
9 google-public-dns-a.google.com (8.8.8.8) 44.316 ms 49.897 ms 49.448 ms
You can also use IPoE
ZOOT NATIVE supports IPv6 native communication in IPoE system together with DS-Lite. Therefore, the IPv6 Internet access by the IPv6 NAPT method with the Cisco ASA 5505 written in this article is also possible.
en-designetwork.hatenablog.com
Conclusion - DS-Lite (IPv4 over IPv6) Internet connection with CentOS
DS-Lite (IPv4 over IPv6) Internet connection to transix (Internet multifeed) via ZOOT NATIVE using CentOS (Linux). As a result, the communication speed to the IPv4 internet network has improved 10 times . Continue to use DS-Lite for free period and consider whether to continue using ZOOT NATIVE.