My colleague said, "I want to study servers at home, but there is only an old PC (32 bit) and I can not build ESXi." In order to provide a verification environment, I built ESXi hosting environment in my home laboratory.
I am using ESXi v6.5 on the server selected in this article and increased the memory to 24 GB, but because I have it, I will cut out a part and try to lend it out.
en-designetwork.hatenablog.com
*If you earn income with home server hosting as a business, you need to confirm the content of the Telecommunications Business Law. Since it is free of charge this time, it does not conflict.
- Network configuration
- Operation confirmation
- Conclusion - ESXi hosting diagram with Home Lab and VyOS
Network configuration
In consideration of feasibility and security, I built a hosting environment in the home lab in the following position. The examination points are as described below.
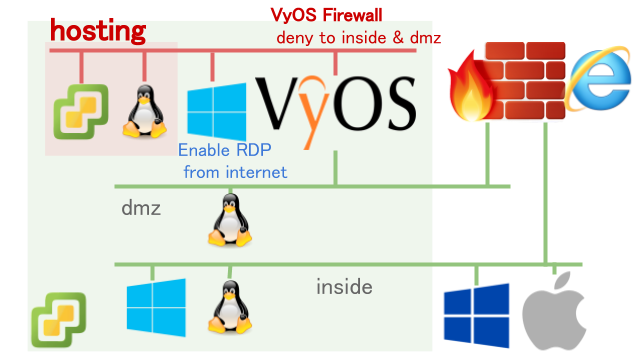
Hosting independent nest ESXi
Hosting is fundamentally borrowed on Linux or Windows server basis. However, I would like to provide an environment that can be freely verified including ESXi (VMware vSphere) this time.
Since it is not preferable for privacy to provide and share your own ESXi, create a new ESXi with nest configuration. (Both ESXi v 6.5)
Users do not need to be conscious of being nested, and you can freely create VMs such as Linux, Windows, virtual appliances on ESXi as usual.
Networking separation of hosting environment
As shown in the figure, the hosting environment is completely separated from my inside, dmz. For network separation, the virtual router VyOS is introduced and segmented. The ASA 5505 wanted to use the CSR, XRV, F5 BIG-IP VE, etc as the virtual router because it was impossible to add the VLAN with the license upper limit, but the free version has the throughput limit (about several Mbps), which is not practical , OSS VyOS was selected.
In addition, from the hosting environment it is only possible to communicate with the Internet, but since we want to maintain the inside-> hosting maintenance, we use VyOS's stateful firewall to implement access control including the direction of communication start .
In this way refusing communication of inside (dmz: 192.168.x.x) after allowing return communication . By accepting default as the default, we allow communication to the Internet as a whole.
set firewall all-ping 'enable' set firewall name hosting default-action 'accept' set firewall name hosting rule 10 action 'accept' set firewall name hosting rule 10 'destination' set firewall name hosting rule 10 state established 'enable' set firewall name hosting rule 10 state related 'enable' set firewall name hosting rule 20 action 'drop' set firewall name hosting rule 20 destination address '192.168.0.0/16'
(Reference information) I have referred to VyOS settings.
Windows Remote Desktop from the Internet
Despite security concerns, we will allow remote desktop to the Windows Server from the Internet with priority on operability. To say enough, if you only provide web access to the ESXi Web Client (vSphere Web Client), you can operate it all at the console, but the copyability and other operations are low. Therefore, once Windows Server is the stepping staircase, VM operation and SSH connection are made from there.
Perform NAT / FW processing with the Cisco ASA 5505 that is used as Internet FW. The public setting in ASA is as shown here (there is room for review). It is written as Web, but it can also be applied to RDP if the port number is changed.
It might be even more convenient if you put it in the hosting segment with VPN ...
*When RDP Win Server is in the hosting environment, it can not operate ESXi restart etc, so it is usually placed in the ESXi environment.
IP dynamic change with DDNS
Since static IP is not yet contracted, in order to connect to the remote desktop from the Internet, home global address can be connected by FQDN using DDNS.
Operation confirmation
We confirmed that the following operation is possible from the Internet by tethering.
- Remote desktop connection from the Internet
- Web access to ESXi from Windows Server
- access to inside, dmz can not
- Throughput (VyOS) is practical
Conclusion - ESXi hosting diagram with Home Lab and VyOS
I built a secure ESXi hosting environment in my home lab. By using Windows Server as a stepping stone, SSH connection to Linux is also a practical environment.
In addition, VyOS used for the hosting environment is simple in setting, secures throughput, I think that it is quite useful for a slight expansion like this time.
Please contact us as we provide a consultation service for the environment. There is no mechanism of automatic deployment and it is manual correspondence.